Microsoft suggests once again to disable the Print Spooler to protect against new 0-day vulnerability
2021-08-15Several Windows printing related vulnerabilities have been discovered, disclosed and resolved in recent time. Microsoft released an emergency update in July to address a vulnerability dubbed PrintNightmare.
This week, Microsoft disclosed yet another printing related vulnerability in Windows. The CVE reveals little information at this point as Microsoft’s investigation is still ongoing.
According to the provided information, it is a remote code execution vulnerability that does affect the Windows Print Spooler.
A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Microsoft does not list the affected versions and editions of the company’s Windows operating system, as research is still ongoing. All versions of Windows were affected by PrintNightmare, and it is possible that the new 0-day vulnerability affects all versions as well.
Microsoft notes that it is working on a security patch, which it will likely release as an out-of-band patch once produced.
Workaround: disable the Print Spooler
Microsoft’s workaround for protecting systems against attacks targeting the new Print Spooler vulnerability is to disable the Print Spooler. The downside to disabling the Print Spooler is that printing becomes unavailable.
One of the PrintNightmare vulnerability workarounds was to stop the Print Spooler as well.
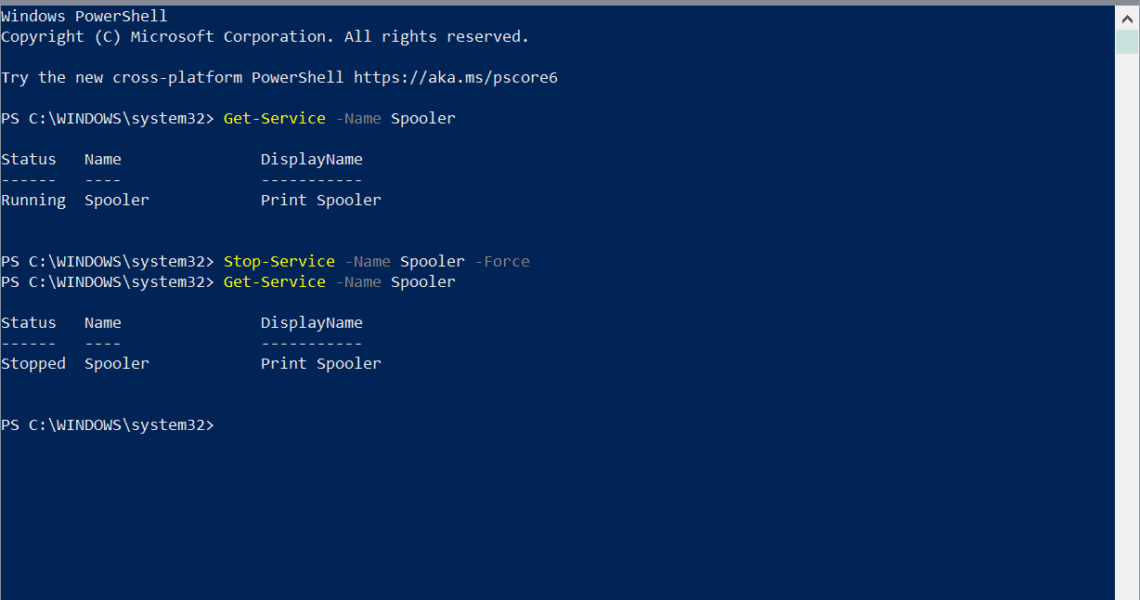
Disable Print Spooler via PowerShell
- Open Start.
- Type PowerShell.
- Select Run as administrator.
- Run Get-Service -Name Spooler to get the status of the print spooler-
- Run Stop-Service -Name Spooler -Force to stop the Print Spooler service.
- Run Set-Service -Name Spooler -StartupType Disabled to set the startup type of the service to disabled so that it is not activated on system start.
Disable Print Spooler via Services

You may also use the Services management interface to stop the Print Spooler service and set its startup type to disabled.
- Open Start.
- Type services.msc
- Locate the Print Spooler service. The list is sorted alphabetically by default.
- Right-click on Print Spooler and select Stop.
- Double-click on Print Spooler.
- Set the Startup Type to disabled.
- Select Ok.
Effect of the workaround
You won’t be able to print anymore on the device if the Print Spooler service is not running. You could enable it on demand, e.g. just the moment before you start a new print job on the device, and turn it off afterwards again.
Summary

Article Name
Microsoft suggests once again to disable the Print Spooler to protect against new 0-day vulnerability
Description
Microsoft disclosed a new 0-day vulnerability of the Print Spooler of its Windows operating system this week; no patch is available, but a workaround has been provided.
Author
Martin Brinkmann
Publisher
Ghacks Technology News
Logo

Advertisement