Here is how to protect Windows PCs from Protocol vulnerabilities
2022-06-02Two days ago, security researchers disclosed a vulnerability in the Microsoft Support Diagnostic Tool that affects all client and server versions of the Windows operating system.
The tool, designed as a tool to communicate with support, is built-in Windows by default. Microsoft confirmed the issue and published a support page to provide system administrators with information on the vulnerability.
The vulnerability exploits an issue in the protocol handling of the Windows operating system. An attacker may exploit it through applications that use the URL protocol to call the Microsoft Support Diagnostic Tool. Successful exploitation of the issue allows attackers to run arbitrary code with the same privileges as the application the attack originated from.
Attackers may use it to install or remove programs from Windows machines, delete or modify data, create new user accounts, access files, or make changes to the Windows Registry.
Microsoft’s workaround for the Microsoft Support Diagnostic Tool vulnerability
Microsoft posted a workaround to reduce the attack surface of the vulnerability. The published workaround does not protect Windows systems completely, as it is still possible to access troubleshooters via the Get Help application and in the system settings.
Here is the official workaround:
- Open the Start Menu.
- Type Command Prompt.
- Select Run as administrator to launch an elevated command prompt window.
- Confirm the UAC prompt.
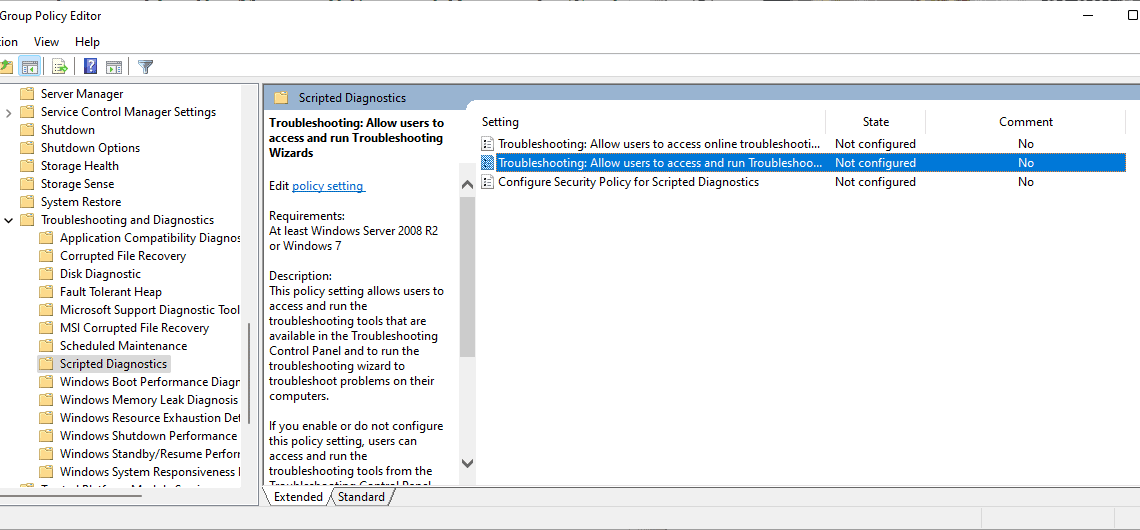
- Run the command reg export HKEY_CLASSES_ROOTms-msdt regbackupmsdt.reg to backup the ms-msdt key. The Registry file is saved to C:WindowsSystem32 by default, but you may add another location in front of the regbackupmsdt.reg file name.
- Run the command reg delete HKEY_CLASSES_ROOTms-msdt /f to delete the key.
You may restore the key at any time by running reg import regbackupmsdt.reg from an elevated command prompt window. Note that you may need to specify the location of the Registry backup file if it is located elsewhere on the system.
Microsoft is asking that customers with Microsoft Defender Antivirus enable cloud-delivered protection and the automatic submission of samples in the application. Microsoft Defender for Endpoint customers may enable the attack surface reduction rule BlockOfficeCreateProcessRule to further protect systems. Enabling the rule blocks Office applications from creating child processes.
Microsoft Defender Antivirus 1.367.851.0 or higher offers detections and protections against possible exploits according to Microsoft:
Trojan:Win32/Mesdetty.A? (blocks msdt command line)
Trojan:Win32/Mesdetty.B? (blocks msdt command line)
Behavior:Win32/MesdettyLaunch.A!blk (terminates the process that launched msdt command line)
Trojan:Win32/MesdettyScript.A (to detect HTML files that contain msdt suspicious command being dropped)
Trojan:Win32/MesdettyScript.B (to detect HTML files that contain msdt suspicious command being dropped)
A better workaround for the Microsoft Support Diagnostic Tool vulnerability
Microsoft’s workaround does not address the vulnerability completely on the system. While it may stop most attacks, it won’t stop all of them as it is still possible to access troubleshooting wizards.
Benjamin Delpy published a better solution on Twitter that disables Troubleshooting Wizards on Windows using the Group Policy. (via Deskmodder)
Windows administrators may change the policy in the Group Policy Editor or by editing the Windows Registry directly.
Group Policy
Note that the Group Policy Editor is only available in professional versions of the Windows operating system. You can check the version by opening the Settings application and going to System > About.
- Open the Start Menu.
- Type gpedit.msc and hit the Enter-key to launch the Group Policy Editor.
- Go to Computer Configuration > Administrative Templates > System > Troubleshooting and Diagnostics > Scripted Diagnostics
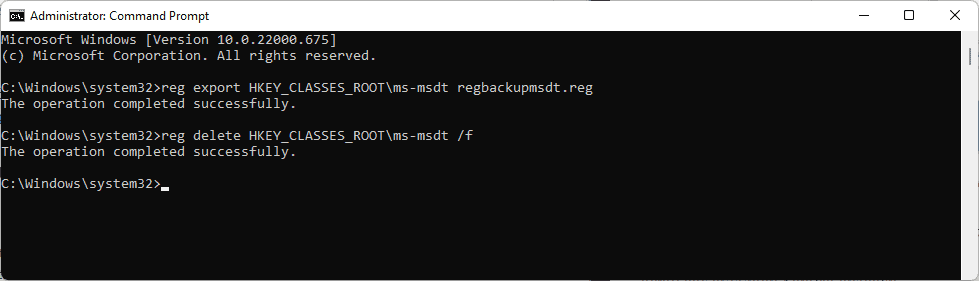
- Double-click on the policy Troubleshooting: Allow users to access and run Troubleshooting Wizards.
- Set the state of the policy to Disabled to block users of the system from launching troubleshooting tools.
- Select OK to complete the change.
The policy is supported on all Windows systems starting with Windows 7 on the client side and Windows Server 2008 R2 on the server side.
Note that this removes the user’s option to run troubleshooters in the system. You may undo the change at any time by setting the state of the policy to Disabled (default), or Enabled. System administrators may want to undo the change once Microsoft lands an official patch in a future update.
Registry Editor
Windows administrators may edit the Windows Registry to disallow the running of troubleshooting wizards on the system; this is the best option on Home systems, which do not support the Group Policy Editor, but some administrators may also prefer the editing of the Registry over the Group Policy.
- Open the Windows Start Menu.
- Type regedit.exe and hit the Enter-key; this opens the Windows Registry Editor.
- Confirm the UAC prompt.
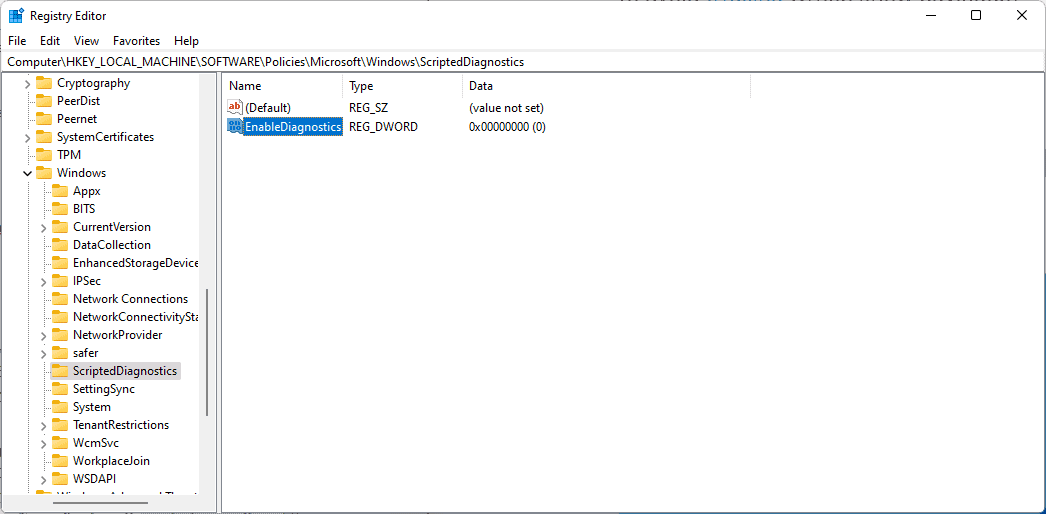
- Go to ComputerHKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsScriptedDiagnostics.
- It is possible that one or more of the listed keys do not exist. You may need to create the missing keys by right-clicking on the previous key and selecting New > Key from the context menu. Repeat the process until all keys are present.
- Right-click on ScriptedDiagnostics and select New > Dword (32-bit) Value.
- Name it EnableDiagnostics.
- Double-click on EnableDiagnostics and set the value of the Dword to 0.
- Close the Registry Editor window.
- Restart the Windows PC to apply the change.
To undo the change, right-click EnableDiagnostics in the Windows Registry Editor and select the Delete option. A restart is required to apply the change.
Windows Search protocol vulnerability
Another vulnerability in the handling of protocols on Windows was disclosed yesterday. The new vulnerability exploits an issue in the Windows Search protocol handler search-ms.
The new vulnerability, disclosed by Twitter user hackerfantastic.crypto, can be exploited to launch a Windows Search window automatically when an Office document is opened. The search window can display executable files on a remote SMB share using names such as Critical Updates to get users to install the malware.
Attackers may also take advantage of the Explorer preview pane and specially prepared RTF documents to launch the search window automatically when the document is rendered in the preview pane of the file manager.
The issue requires user interaction, but it could still lead to the infection of user systems if users are not careful about what they open on their devices.
Microsoft has not confirmed the new issue yet. Administrators may block it by deleting the search-ms protocol handler in the Windows Registry:
- Open the Start Menu.
- Type Command Prompt.
- Select Run as administrator to launch an elevated command prompt window.
- Confirm the UAC prompt.
- Run the command reg export HKEY_CLASSES_ROOTsearch-ms search-ms.reg to backup the Registry key.
- Run the command reg delete HKEY_CLASSES_ROOTsearch-ms /f to delete the Registry key.
- Close the Registry Editor.
- Restart the PC.
To restore the functionality, run reg import search-ms.reg from an elevated command prompt window.
Summary
Article Name
Here is how to protect Windows PCs from Protocol vulnerabilities
Description
Instructions for Windows client and server administrators to protect Windows devices against protocol vulnerabilities.
Author
Martin Brinkmann
Publisher
Ghacks Technology News
Logo

Advertisement